Explore crypto articles
to learn about digital currencies and how they work.
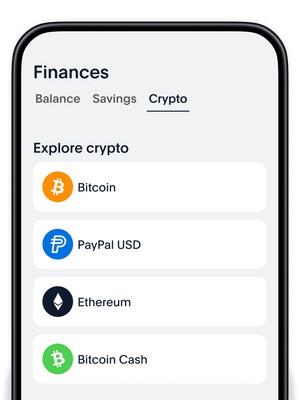
Go to Finances
and select Crypto from the dashboard.
Choose your crypto
select Buy, and choose the amount you’d like to purchase.
Use the app to buy, transfer, and sell cryptocurrencies: Bitcoin, Bitcoin Cash, Ethereum, Litecoin, and the new PayPal stablecoin, PayPal USD (PYUSD).1
PayPal works to prevent unauthorized transfers of cryptocurrency, and you may be eligible for reimbursement up to an equivalent of $50,0002 in the event of an unauthorized transfer.
Read our latest articles and know the basics about crypto directly from the app.
Check out at millions of online stores and crypto marketplaces, track market fluctuations in the app, or transfer your crypto into your PayPal Balance account3 or to a friend— all in just a few steps.
1 USD : 1 PYUSD on PayPal
PayPal USD is backed by secure and highly liquid assets. Buy, sell, hold, and transfer it in our app and on our site. Or use the convert feature to buy the cryptos we support. Fees apply.4
Buy and sell cryptocurrencies directly from crypto wallets with the comfort of PayPal.
to learn about digital currencies and how they work.
and select Crypto from the dashboard.
select Buy, and choose the amount you’d like to purchase.
Make your crypto move.
Use your crypto on eligible purchases at millions of online stores worldwide. Get set up today.
Complete your W-9 tax form in advance in the app to use your crypto as a payment method.
Crypto is automatically available as a payment option as long as you’re able to pay in full.
We’ll convert the crypto amount into USD, or to the seller’s currency, at no additional fee.4
Easily and securely spend, send, and manage your transactions—all in one place. Download the app on your phone or sign up for free online.
Scan the code or enter your number to get the app.